Rule
Rule Type
You can add rules from the Antom Dashboard in the Risk menu bar by clicking Risk Strategy. You can configure the following rule types:
- 3D Secure (3DS) rule: The risk control outputs the 3DS authentication request. It is generally recommended that the 3DS verify the request before proceeding with the payment process.
- Acceptance rule: The risk control directly allows payment requests that meet the rule.
- Rejection rule: The risk control directly blocks payment requests that meet this rule.
Note:
- When a payment request meets multiple rule conditions, Antom will output the final decision result in the priority order of 3DS authentication > accept > reject.
- When the same payment request meets your configured list and rule conditions, the list takes precedence over the rule.
- Configuring an overly simple approval rule means that all transactions that meet the rule will be directly accepted, which may pose additional risks. Therefore, please ensure that the rules are thoroughly evaluated by you before deployment.
Rule classification
When creating rules, you can refer to the following risk control rule categories:
- Cumulative rule: The cumulative rule is evaluated based on the frequency of variables matched within a specific time window, which can be set to different time periods, such as daily, weekly or monthly. Examples of rules include:
- High-frequency trading alert: Triggers 3DS authentication if a user attempts to pay more than 5 times in a day.
- Repeat purchase alert: If the same shipping address is used by more than 5 users for payment, the transaction will be rejected.
- Conflict rules: Rules that check for inconsistencies in transaction information, such as:
- Receiving address verification: Triggers 3DS authentication if the billing address is inconsistent with the shipping address.
- Card issuing country validation: Triggers 3DS authentication if the order's receiving country does not match the country of the credit card issuing bank.
- Risk scoring rules: Using machine learning models, Antom comprehensively evaluates trade information and generates risk score recommendations. Based on the score, you can decide whether you need further verification or reject the transaction. For example:
- Transactions with a machine learning model score of more than 80 points will be considered as high-risk transactions, and thus rejected.
- Transactions with a risk score between 50 and 80 will trigger 3DS authentication.
- Original variable rule: The rule is set directly based on specific fields in the transaction data (such as card BIN, user mailbox, etc.). For example:
- Card BIN: If the transaction comes from a list of known malicious card BIN attacks, the transaction is rejected.
- Trusted mailbox: If the user's mailbox is detected to match a known trusted mailbox, the transaction is allowed to go through.
Rule configurations
- After selecting the rule type, create the rule.
Enter the risk menu and click the risk tool on the rules page, select the corresponding rule type, you can create your rules on our user interface here.
- Quickly validate rules in the Rule Editor.
On the rule editing page, after saving the rule, you can use the Test button in the upper right corner to manually enter transaction data for quick testing to verify that the configured logic meets expectations.
- Save and test rule.
Save the created rule and test run it.
Antom Shield provides real-time online rule commissioning capabilities. Among them, the rules in the trial run state will only record the results of the execution for effect evaluation, and will not actually affect the decision-making results of the transaction.
- Publish rules online.
After the test run, if the effect of the rule meets your expectations, you can publish the rule online. Upon launch , if the rule is matched, it will directly affect transactions outcomes on subsequent transactions.
Best Practices
To maximize the effectiveness of the risk control rules, Antom recommend the following best practice strategies.
Combined application of multiple rules
The use of a combination of the same or different types of rules, such as a combination of cumulative rules and risk scoring rules, can effectively monitor the frequency of abnormal transactions and use intelligent algorithms to assess risk. You can refer to the following examples:
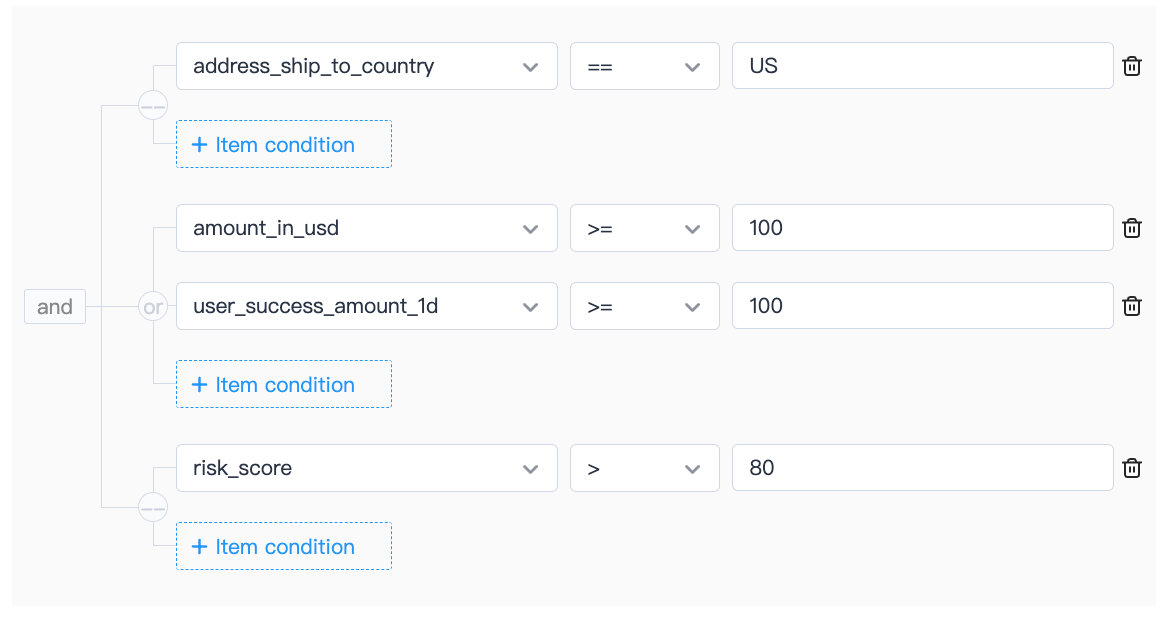
When your store has a fraudulent chargeback order from the United States, it usually shows up as a single transaction amount or a user's cumulative payment amount exceeds $500 in a single day. To reduce similar fraudulent transactions, you can configure the following reject rules:
- For orders with mailing addresses in the United States, when the user's single order amount exceeds $100, or the user's cumulative payment in a day exceeds $100, and the risk score is higher than 80, the transaction is rejected. The transaction is rejected if the following conditions are met:
Continuous optimization of rule sets
As the business grows, risk patterns faced by the business continue to change. Periodically review the performance of existing rules, and adjust rule parameters based on the latest market trends and technological developments.
Monitor rule hit rate
Pay close attention to the matched rates of each rule, remove rules that hasn't been matched in a while to maintain system efficiency.
Leverage the test run function
Antom Shield provides real-time online rule test runs. After the rule configuration is complete, you can perform a trial run to observe the hit status and effect analysis of the rule. This process not only helps you evaluate the validity of the rules, but also ensures their reliability and accuracy in real-world applications. In addition, during the pilot, you can adjust and optimize the rules in real time to better adapt to business needs and risk management strategies. In this way, you can keep your business running smoothly while taking full control of possible risks.
